Hackthebox: Checker

Overview
Checker is a hard-difficulty machine from Hack The Box dealing initially with an exposed Teampass instnace allowing us to exploit CVE-2023-1545 which is a SQLI allowing us to read users’ password hashes which then gives us access to Teampass where we find ssh creds that need a google authenticator OTP and Bookstack instance credentials. We’ll then exploit CVE-2023-6199 with php filter chain for LFI to be able to read the Google OTP code allowing us ssh access. Finally we’ll abuse an SHM Race Condition allowing for command injection to become root.
Reconnaissance
1 | Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-26 17:39 W. Central Africa Standard Time |
We can see that we have our usual ssh 22 port alongside two web applications, one deployed on port 80 and the other on port 8080.
Web Application - http://checker.htb:8080
Checking the web application deployed on port 8080, we can see that it’s an instance of Teampass which is a Passwords Manager dedicated for managing passwords in a collaborative way by sharing them among team members.
There was no apparent way of logging in or creating an account, so I went looking for exploits:
CVE-2023-1545 - SQL Injection in Teampass versions >=0.0.0, <3.0.10
Looking into potential unauthenticated vulnerabilities, I managed to find this SQLI great post alongside a poc. Let’s see what we can do with it:
1 | kujen@kujen:~$ ./sqli_checker.sh http://checker.htb:8080/ |
And just like that we managed to get two users password hashes. We managed to crack bob’s hash with JohnTheRipper:
1 | ─(kali㉿kali)-[~] |
We can now use it to login on the portal: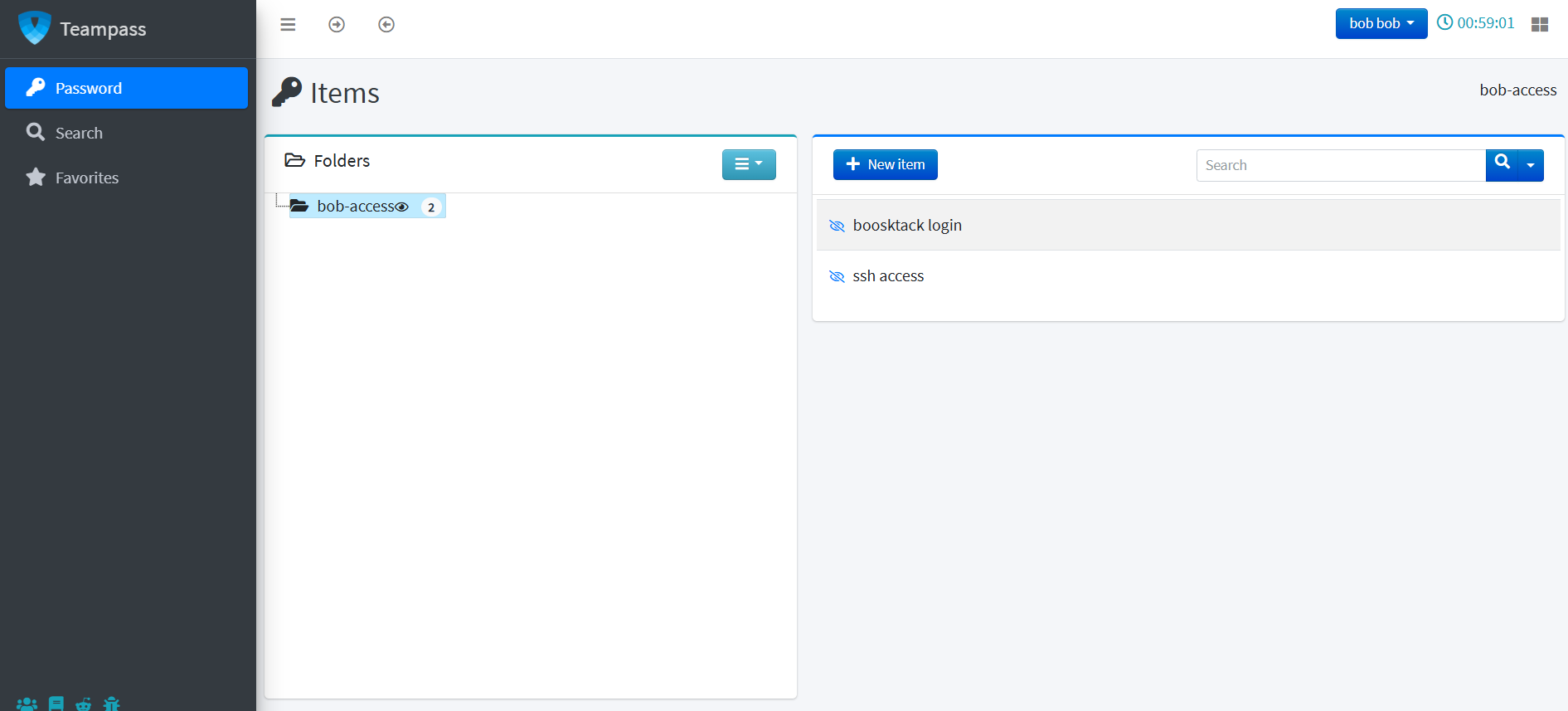
Navigating through the account, we managed to get ssh credentials for a reader user and bookstack (http://checker.htb ) credentials for bob: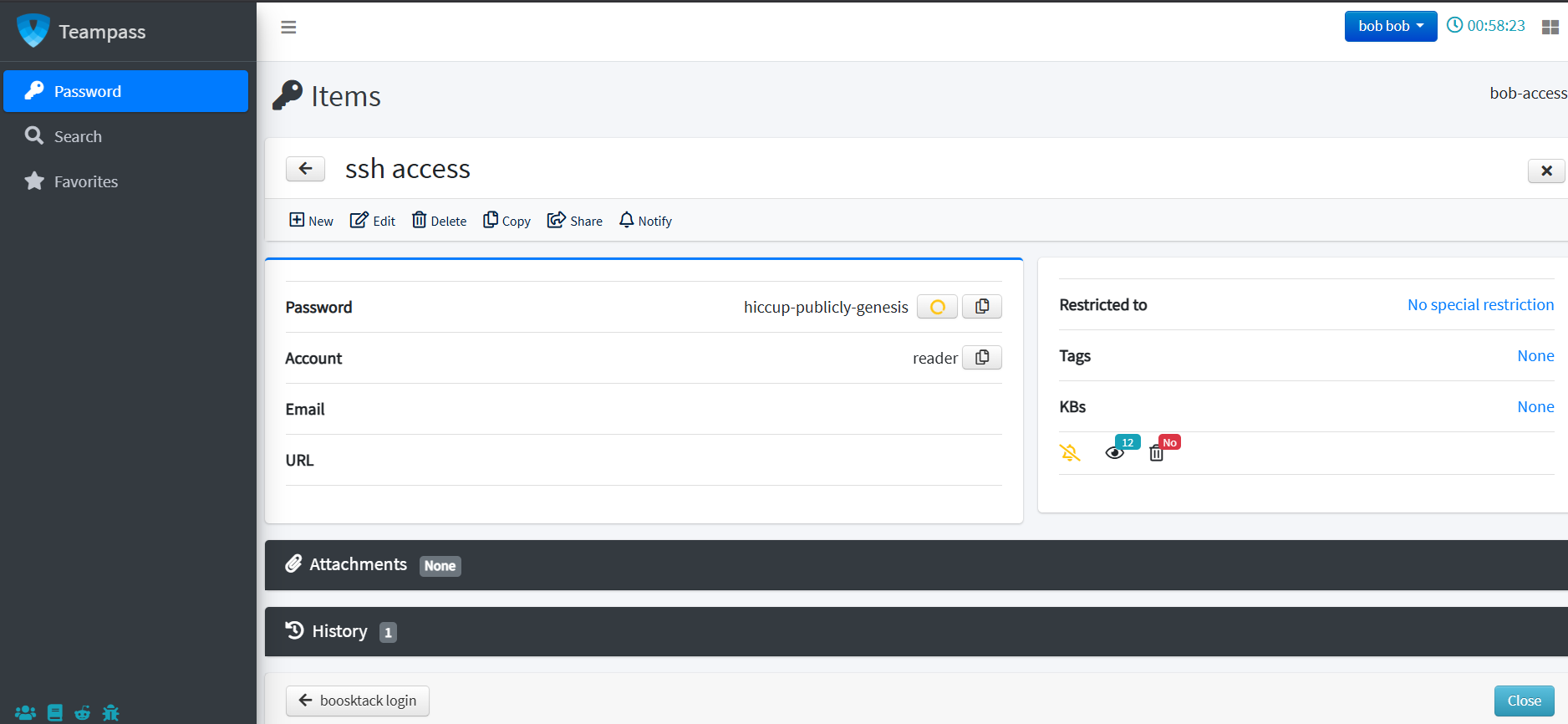
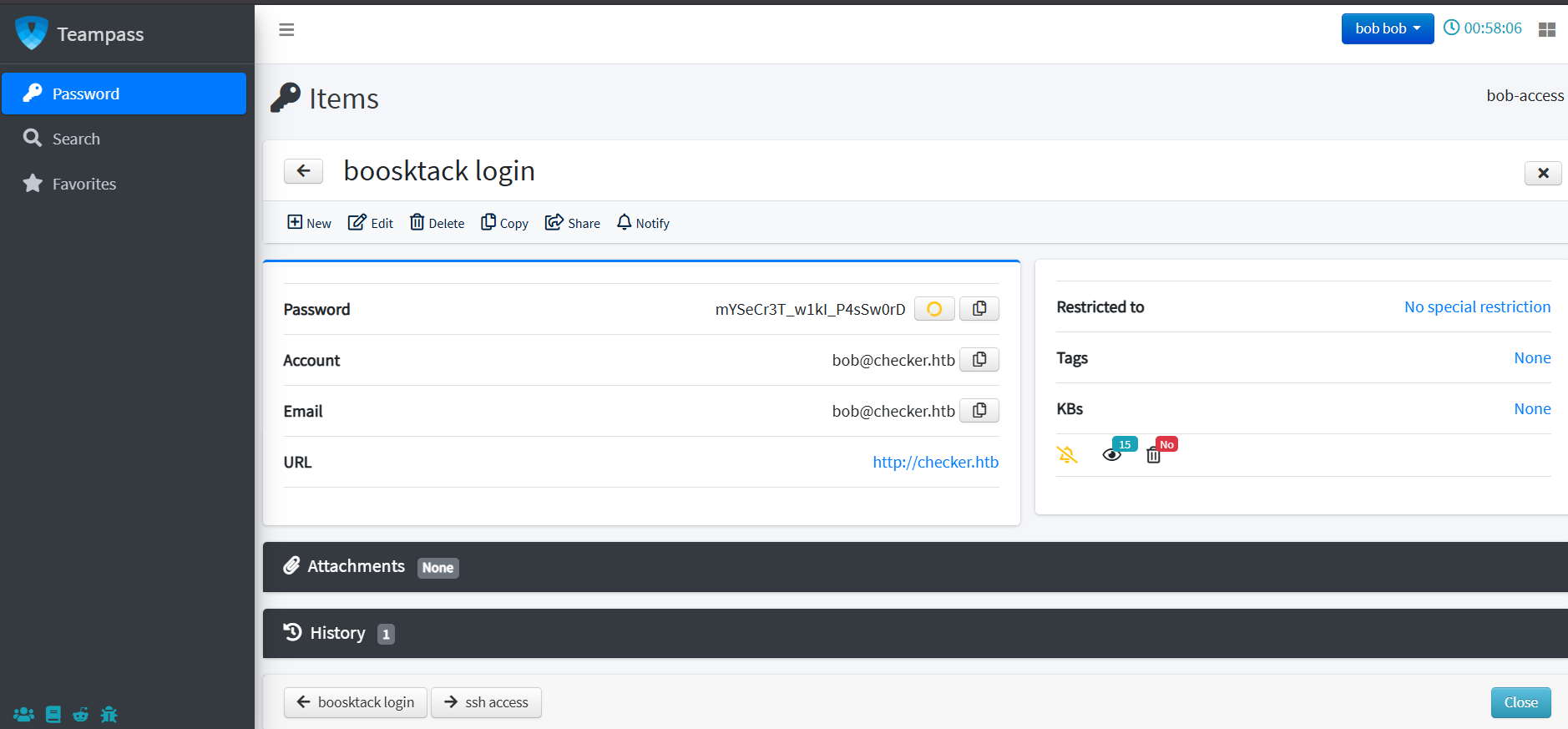
Bookstack Web Application - http://checker.htb
We can now use those credentials to access the bookstack endpoint using bob:
Chaining Bookstack CVE-2023-6199 with php filter chain for LFI
Looking into Bookstack, I stumble upon this CVE detailing how Book Stack version 23.10.2 allows filtering local files on the server. This is possible because the application is vulnerable to SSRF.
I will then use this script from Synacktiv team but I’ll just have to modify this small section in order for it to work:
1 | def req_with_response(self, s): |
Now what we’ll have to do it:
1- make a book
2- make a page in the book and save it as a draft
3- get x-csrf and xsrf and bookstack cookies from it
And run our script to get the google authenticator code that’ll be used for ssh access:
1 | kujen@kujen:~/php_filter_chains_oracle_exploit$ python3 filters_chain_oracle_exploit.py --target "http://checker.htb/ajax/page/10/save-draft" --file "/backup/home_backup/home/reader/.google_authenticator" --parameter "html" --verb PUT --headers "{\"X-CSRF-TOKEN\": \"RU9rQ6JdJkCLFAOCazBi5gK6GyMi7vFU8Qg5zWOp\", \"Content-Type\": \"application/x-www-form-urlencoded\", \"Cookie\": \"jstree_select=1; XSRF-TOKEN=eyJpdiI6IjAzcWFWOEF5UGdoWUVRVTA1L096NUE9PSIsInZhbHVlIjoiN0ZoZHp1cVRWbkZ2VEliNDNrY0x2c3JOYTAydTBpNUdyckFrTFNXdmUrOE83STNBSU9Ec1dPZ3dTRlQ2RUxmZWIyMEFLb1FNYzBLN3gxUDlOaWNUSFlhRXF1ZnVBdUVYZFJCY3hZQ21LbVFvdWpKM0NkZ0FLQktyNCs2WndST0MiLCJtYWMiOiJkZTljNDk3NzliMmYyN2Y5OTQ2NGI0YjVjZGE2ZTQ2ODU4ZjkwMjQxODhiNTBjMzBkOWQxZTNiYzcyNGVkYjI3IiwidGFnIjoiIn0%3D; bookstack_session=eyJpdiI6Illtc2JkbkUzYWVPWUxVQUp2a0UwdWc9PSIsInZhbHVlIjoiMFRHcG8wdGczeEw1cDBOc2xXcDRCeHRxT0dCYldLY3JRMzNpRDVVbUUrWExZK2ttWXlOdUxJWkhNWFJ2WUNDYWVQTkFoS2YxZGZnbVoraEhuV2pYcStLZVRJZmNXZTlIckJtRi9xS0JqbXhRM1RkRldQcDJJNHY5YXVFcDhNL2oiLCJtYWMiOiJjMzA0YzY5NWQ2ZWFkYmYzMGI1MDFmNjkxZDllODBlMDA5ODNjNDY0NTRiNDJlMzZjZTE0ZGFmZDdmYjY0NjU2IiwidGFnIjoiIn0%3D\"}" |
The location of the code can be found in the documentation for the plugin.
Now just insert that code into https://it-tools.tech/otp-generator and ssh with it:
1 | reader@checker:~$ id |
Privilege Escalation - SHM Race Command Injection
Checking what we can run as sudo, we find an interesting script that’s actually executing a binary:
1 | reader@checker:~$ sudo -l |
We have got to decompile the /opt/hash-checker/check-leak binary with ghidra and analyse what it’s actually doing.
So the program checks hashes on the DB against a list of known hashes /opt/hash-checker/leaked_hashes.txt but does that using shm memory with read/write permissions for everyone. What we basically have to do is change what the program stores in memory so that we can inject a command that’ll get executed by the program itself.
The write_to_shm() function writes to a random selected memory location, and the notify_user() function calls popen() using the string stored at that memory location. There is a one second sleep between them
The key for the shmget() call is the result of a call to rand(), and srand() is seeded with the current time()
The notify_user() function is given the randomly-selected key value, so it can get a handle to that memory location. This function searches for Leaked hash detected and locates the position of the > char. This is so it can search the database for the matching password hash$
The format string eventually passed to popen() is: mysql -u %s -D %s -s -N -e 'select email from teampass_users where pw = "%s"'. If we can control this final ‘%s’ value, within the 1 second, we’ll be able to achieve command execution.
Thanks to dear Chatgpt we’re able to make this:
1 |
|
I delete the GPT comments to look cool 8)
Now we just compile that. Then one one shell we run while true; do ./test; done and on the other we run sudo /opt/hash-checker/check-leak.sh bob
And we get what we want:
1 | reader@checker:/tmp$ ls -al /bin/bash |
And that was it for Checker. I wish I could make a more detailed writeup but I’ve been sick for a week now :(
Hope you learned something new <3
-0xkujen
- Title: Hackthebox: Checker
- Author: Foued SAIDI
- Created at : 2025-05-30 17:31:55
- Updated at : 2025-05-30 22:25:12
- Link: https://kujen5.github.io/2025/05/30/Hackthebox-Checker/
- License: This work is licensed under CC BY-NC-SA 4.0.